Showing posts with label supported. Show all posts
Showing posts with label supported. Show all posts
Tuesday, 5 September 2017
How To Repair imei A20 a13 a10 Mtk cpus supported Tablet Device Guide
How To Repair imei A20 a13 a10 Mtk cpus supported Tablet Device Guide
Advance Tablet imei repair tools V1.0
supported allwinner A20 cpu
supported allwinner a10 cpu
supported allwinner a13 cpu
supported Mtk 6572,65xx cpu
suppotred allwinner 2g modem imei writing
supported allwinner 3g modem imei writing
Different imei writing tools for different modem version
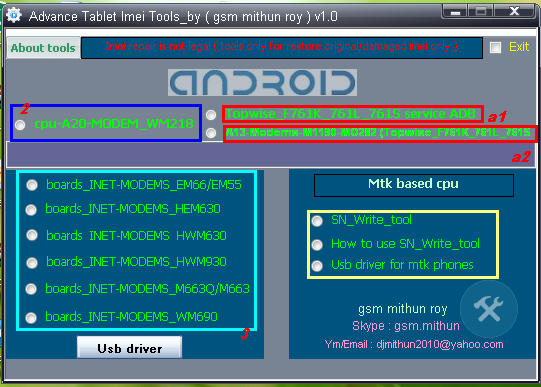
note : All tools need usb debugging on
For any tablet imei repair
supported allwinner A20 cpu
supported allwinner a10 cpu
supported allwinner a13 cpu
supported Mtk 6572,65xx cpu
suppotred allwinner 2g modem imei writing
supported allwinner 3g modem imei writing
Different imei writing tools for different modem version

note : All tools need usb debugging on
For any tablet imei repair
How to use :
A1 & a2 : Click a1 topwise_F761k_761l_761s service Adb copy or extract Dragonface_v10 folder to desktop > open folder and deagonface.exe,now close advance tablet imei tools and open tool aagin now click a2 a13 modems1190-m0228 (topwise_F761k_761l_761s) then connect tablet and repair
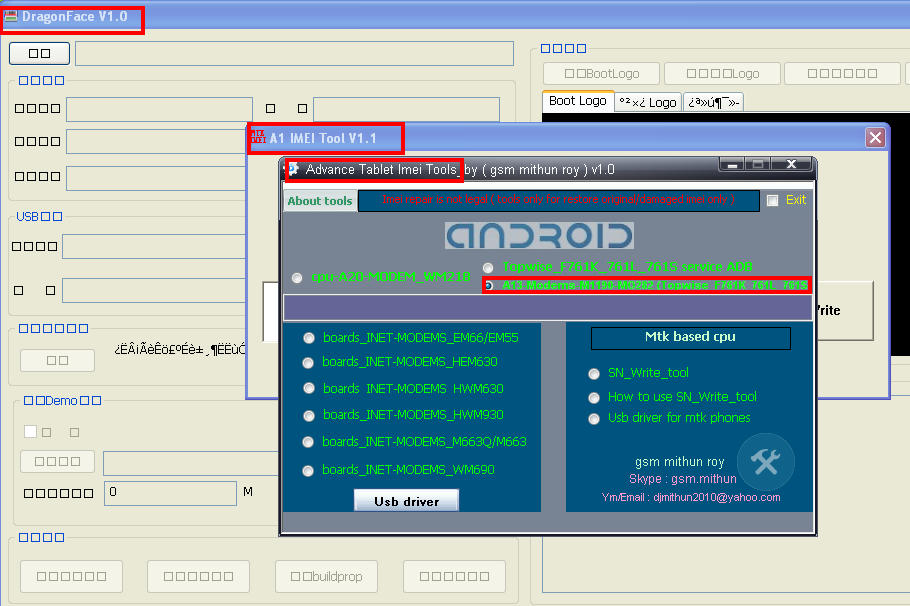
A1 & a2 : Click a1 topwise_F761k_761l_761s service Adb copy or extract Dragonface_v10 folder to desktop > open folder and deagonface.exe,now close advance tablet imei tools and open tool aagin now click a2 a13 modems1190-m0228 (topwise_F761k_761l_761s) then connect tablet and repair


2 : just click and fill the box imei digit press write
3 : click to any tools
according matches su al modem device enter 15 digit imei in cmd tool press enter then restart device and check
DOWNLOaD
download file now
Wednesday, 9 August 2017
Android Security Update for January 2017 Released for Supported Devices
Android Security Update for January 2017 Released for Supported Devices

A nother month, another Android Security Update. Google has actively been taking steps to find and disclose security issues during their monthly Android Security Bulletins. The current situation in the world of Android security, at least from Google�s end, is a lot better than before such bulletins were released.
Right on time, the security patch for January 2017 is now live. All supported devices can look forward to receiving an OTA with the update that patches a lot of security holes. The complete security update marked for January 5th, 2017 contains patches for 10 vulnerabilities marked critical, 28 marked as high severity, and 12 marked as moderate severity in total.
Google notes that the most severe of the patched issues is a Critical vulnerability that could enable remote code execution on an affected device. This remote execution could be initiated through multiple methods such as email, web browsing, and MMS when processing media files. The good news is that Google has received no reports of active exploitation or abuse of these reported issues in the wild.
If you are interested, you can read the complete security bulletin for the month of January found here.
 |
| Share this post |
download file now
Subscribe to:
Posts (Atom)